Built for Speed. Designed for Regulatory Confidence
Unified Third-Party Risk
Management SaaS
Faster Diligence. Stronger Control. Audit-ready by design.
Designed for Risk, Audit & Compliance Teams
🔹 Enterprise Ready
🔹 SOC2 Focused
🔹 Built by GRC Experts
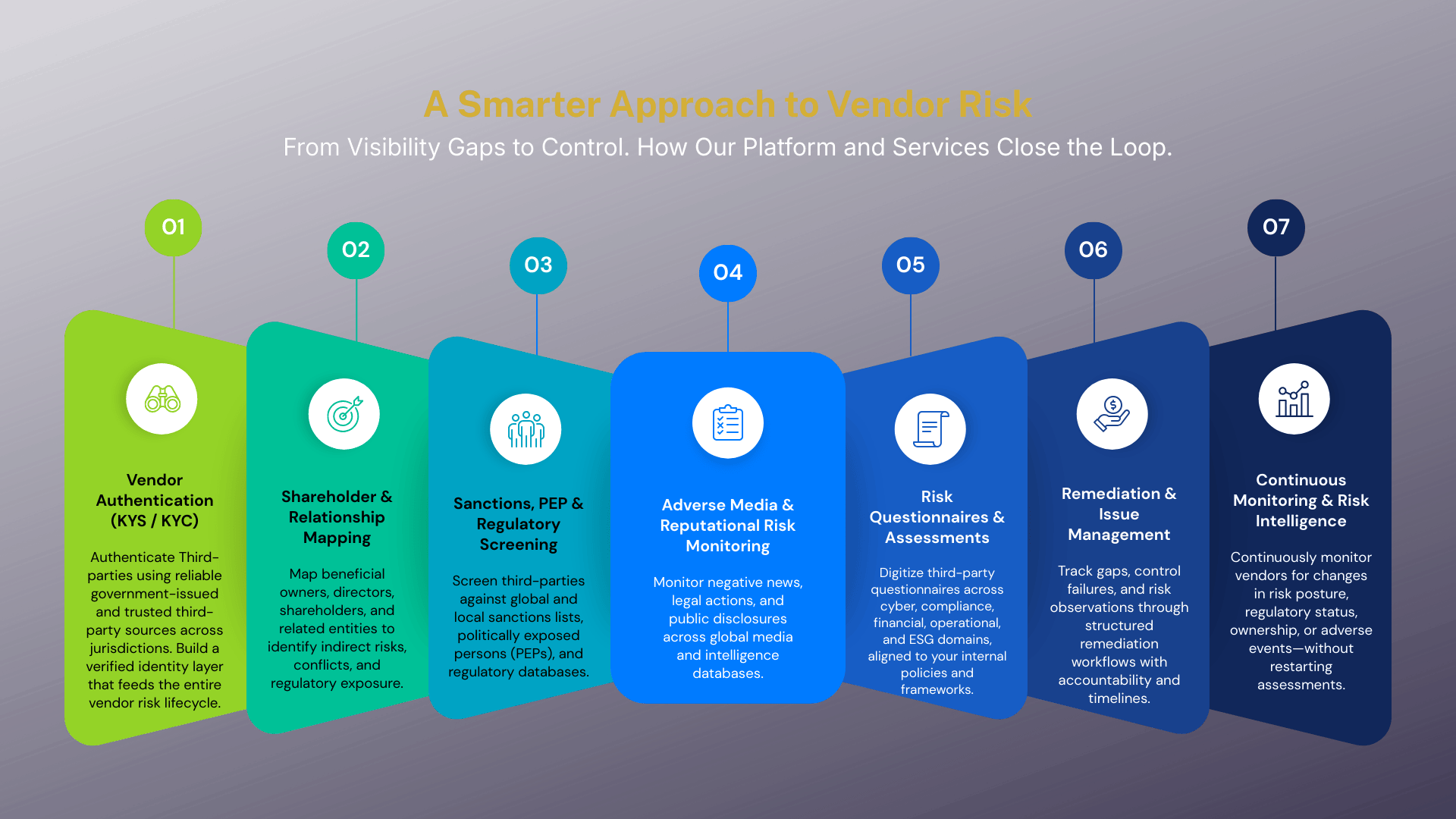
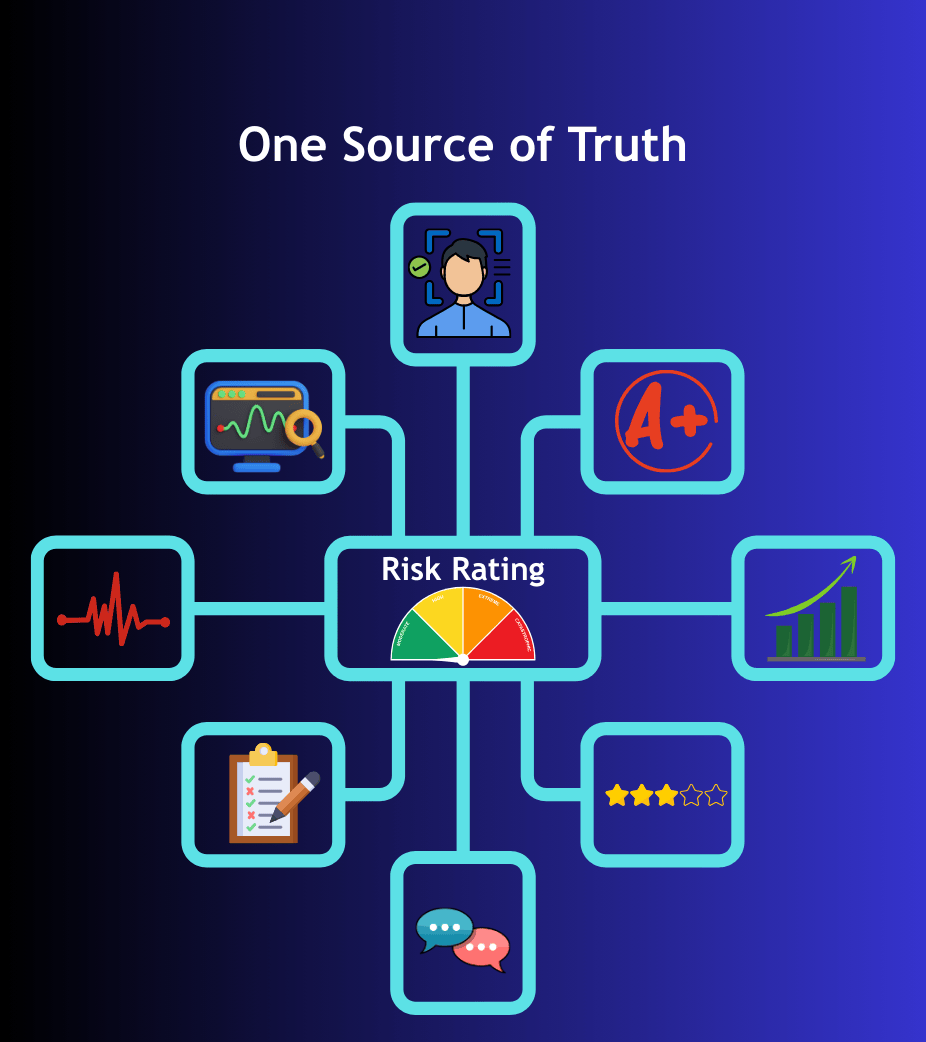
Single Source of Vendor Truth
Vendor information
flows from ERP or onboarding forms & is reused across the entire vendor risk lifecycle — eliminating duplicate data collection.
Vendor Authentication
• Vendor Verification
• Automated Risk Scoring
• Vendor Communication
• Workflows
• Audit Trails
• Real-time Dashboards
Operational & Regulatory Outcomes
The Complete Toolkit to Build, Launch & Scale
Our platform transforms how enterprises approach Third-party Governance, Risk, and Compliance.
Modern, intuitive, and designed for today’s fast-paced regulatory environment.
Automation & Rules-Driven Intelligence
Eliminate fragmented spreadsheets and email-based checks. Centralised risk workflows, rules-based screenings, and structured evidence repositories enable teams to manage large vendor ecosystems efficiently—without increasing headcount.












































From Manual Checks to Continuous Risk Intelligence
Crest Intelligence automates data collection, risk scoring, and alerts across third parties. Move from one-time diligence to continuous monitoring, enabling teams to focus on high-risk vendors and regulatory priorities.
Faster Due Diligence. Stronger Control
Crest’s intelligence-driven workflows streamline vendor onboarding, risk checks, and ongoing monitoring. Review cycles are shortened while every decision remains documented, defensible, and audit-ready—without slowing business operations.
Reduce Vendor Risk Cycle Time & Manual Effort
Automate repetitive third-party risk tasks—vendor discovery, screenings, questionnaires, and evidence collection. Reduce manual effort across procurement, risk, and compliance teams, allowing them to focus on risk decisions, escalations, and governance instead of chasing data.
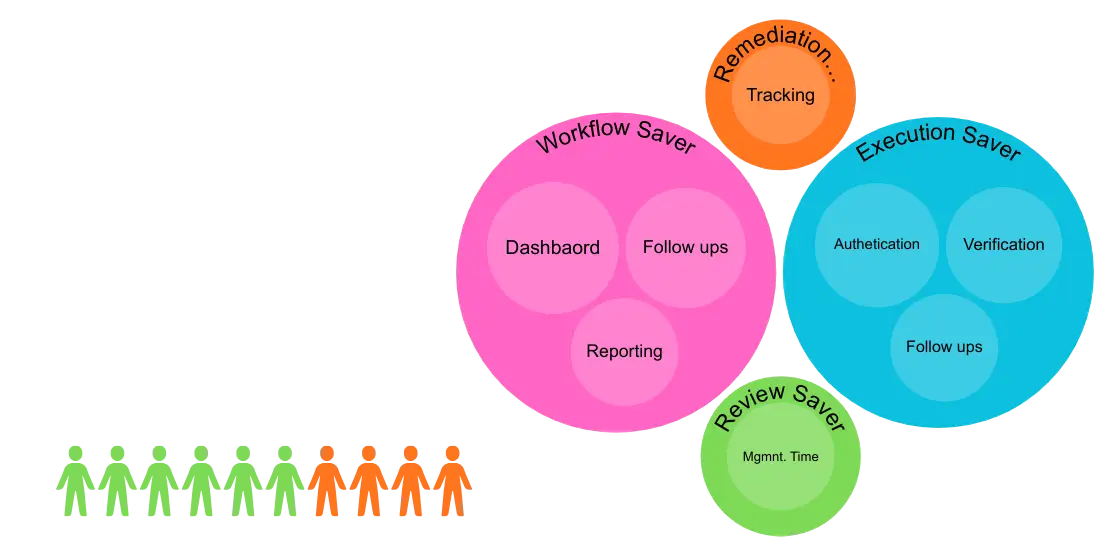
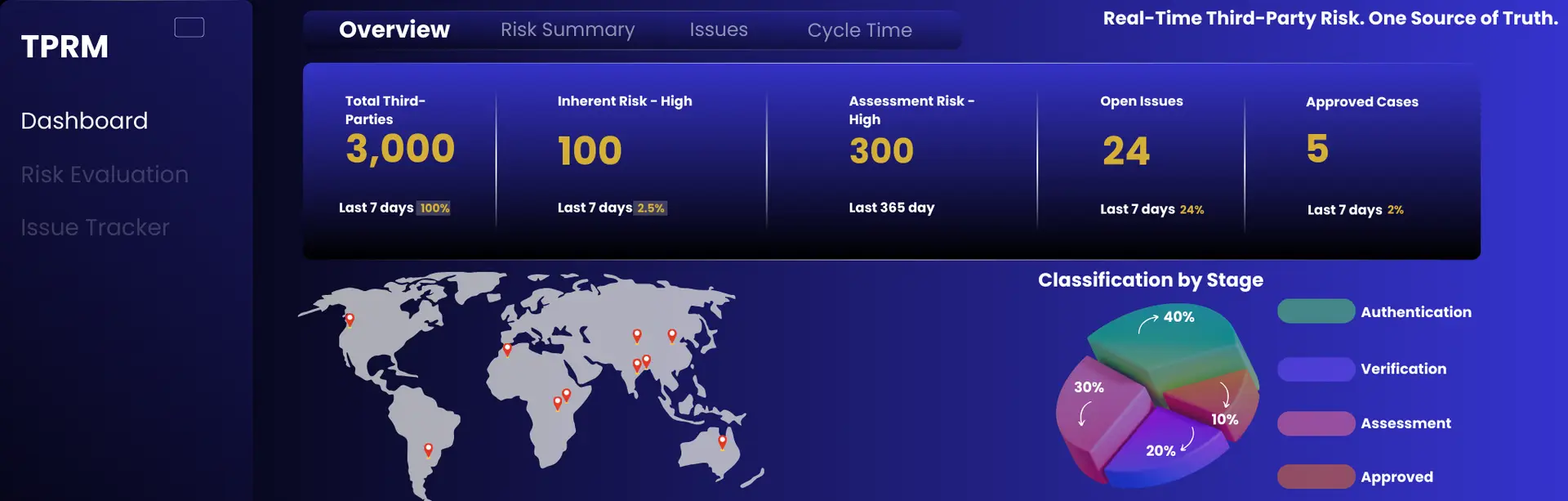
Early Risk Detection. Actionable Insights
Real-time CXO visibility into vendor risk exposure, open issues, required actions, and concentration risks—without manual MIS or PPT reporting.
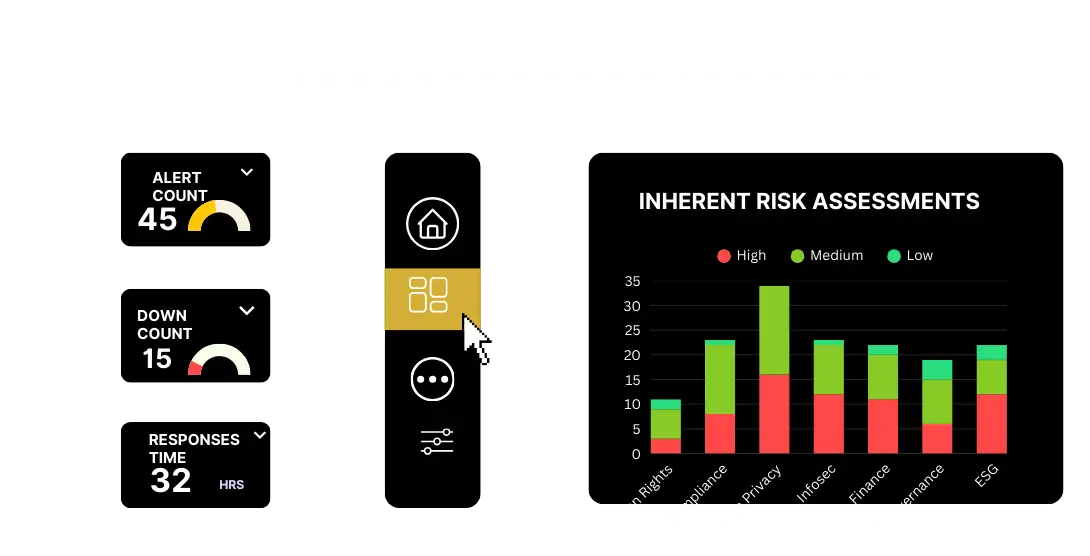
Enterprise-Grade Risk Intelligence
Built on Trusted, High-
Integrity
Data Sources
India Courts Data
+ Local Authorities
Global & Country watchlists
250+ jurisdictions
PEP Count
150+ Languages
Articles
45+ Languages
ESG Risk Factors
120+ Countries
Global Sanctions List
120K+ Entities Covered